Introduction to TACF
This chapter describes TACF’s key functions, structure, and interaction with the rest of the OpenFrame system.
1. Overview
OpenFrame/TACF stands for Tmax Access Control Facility (hereafter TACF). In OpenFrame, this module is responsible for handling user authentication, resource access control, and logging resource access statistics. TACF protects the system from unauthorized intrusions by managing the list of registered users and system authorities.
TACF records user and resource access histories as logs. The logs are used as the source data for statistical information.
TACF provides the following functions.
-
User Authentication
Users who attempt to access the OpenFrame system must enter a valid user ID and password. The purpose of the user ID is to identify the user, while the password confirms that the user is the actual owner of the account. Only users with a valid user ID and password can access the system. This process is referred to as 'user authentication.'
-
Resource Access Control
Even if a user has a valid ID and password, the administrator must have granted them authority to access specific resources. The resources that can be accessed by each user can be managed individually for each user, or user group. The TACF protects system resources by preventing users from accessing resources that they do not have the authority to access.
-
Logging
TACF records a user’s system access time, access count, and statistical information about used resources. These logs are the source of analyzing resource usage and the degree of resource exposure.
2. Structure of the TACF System
TACF stores user and resource information in a "profile" that takes the form of a table in the system’s Relational Database Management System (RDBMS). When managing user authentication and resource access, TACF must access this profile in order to read, register, modify, or delete entires.
During periods of frequent resource access, TACF must frequently access the DB (where the resource profiles are stored). Frequent access can be redundant (as most profiles are not often changed) and may hurt system performance. To avoid this, TACF caches profile information in memory. This enables TACF to refer to the information in memory, minimizing the load on the DB and improving system performance.
TACF can handle authentication and authorization in diverse system environments because it uses both CS (client/server) type and API type interfaces.
In the case where a client requires that user ID or password be customized to account for specific circumstances, TACF functions do not have to be modified. This is because TACF provides a plug-in type SAF_EXIT module. This module provides an interface for communicating with client-tailored APIs, enabling customized rules to be used without modification of TACF internal modules. Once a user has accessed the system, TACF stores their authentication information as an ACEE (Accessory Environment Element). An ACEE records information about the user such as password, attributes, connected-group, etc. The ACEE is deleted from the system when the user logs out.
The following is the structure of TACF (solid lines represent API call paths and dashed lines represent service call paths. Arrows indicate the direction of resource movement.).
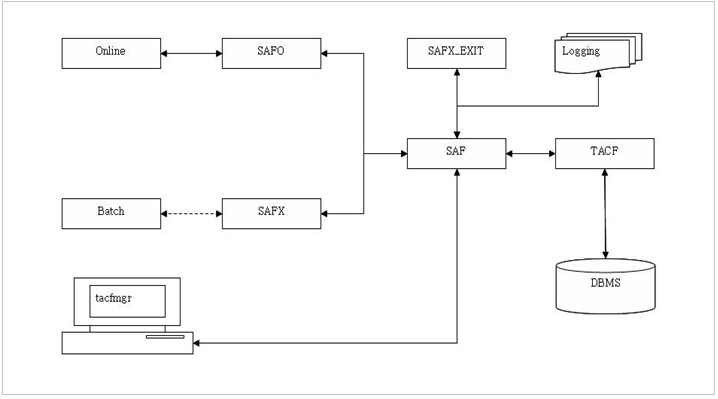
-
SAFO
SAFO is a client interface API that enables clients to request specific services. As the client and server exist in the same node, SAFO can be used without accessing Tmax services.
TACF returns a serial SACEE instead of a token to clients who have successfully been authenticated.
-
SAFX
SAFX is a client interface module that is a Tmax-type service. After TACF verifies that a user has authority to access the system, it returns a token to the client. Using tokens reduces the network load and prevents leakage of user information (compared to using ACCESS). Tokens are deleted by TACF once the user logs out.
-
SAF
The SAF module handles the connection between external interfaces (SAFO and SAFX) and TACF. This module creates and manages the ACEE and records TACF access history information.
-
TACF
TACF retrieves authenticated user information from the ACEE (such as password, attributes, and connected-group). TACF is the module that performs the actual user identification, authentication, and resource access control processes.
-
SAF_EXIT
SAF_EXIT facilitates the customization of ID and password rules and standard TACF functions.
If the system uses additional/customized user ID or password rules, this module checks whether the provided information complies with the rules.
-
tacfmgr
tacfmgr (TACF Manager) is a utility for TACF management. It facilitates the addition of new users, registration of new resource profiles, and so on. For more information, refer to TACF Commands.
3. TACF and the OpenFrame System
OpenFrame Online applications and OpenFrame batch programs interact with TACF differently. For Online systems, authority is verified through the API provided by TACF.
For batch programs, when a job authenticates a user defined in JCL, or a user attempts to access a resource, OFRSASVR (Tmax server) sends an authentication or access control request to TACF.
The OpenFrame Batch tools and utilities, however, directly call the TACF API (without using the Tmax OFRSASVR server).
4. Starting and Shutting down TACF Server
There can only be one TACF server active in each domain. Therefore, before TACF server is started, the administrator must determine which node in the domain TACF server will run.
If a TACF server is already active in the domain, it must be terminated before starting a new TACF server. Before starting TACF server, confirm the database specified in the [SYS1_ODBC] section of dbconn.conf, which is an integrated management file for database connection.
If the database is unavailable, the backup database can be used instead. If this backup database is also unavailable, TACF server cannot be started.
Do not shutdown TACF server while a batch process is underway. This may cause errors in the process.